After the user account is created, operations can be performed on ClusterJ with a session.
ClusterJ Security Doctrine
ClusterJ security will evolve based on a set of values and principles:
Values
- Prevention
- Tracking
- Protection
Principles
- Randomness
- Diversity
- Customization
This aspects will be described here and other ClusterJ’s social networks and will be the base to criticism, defense and development of itself.
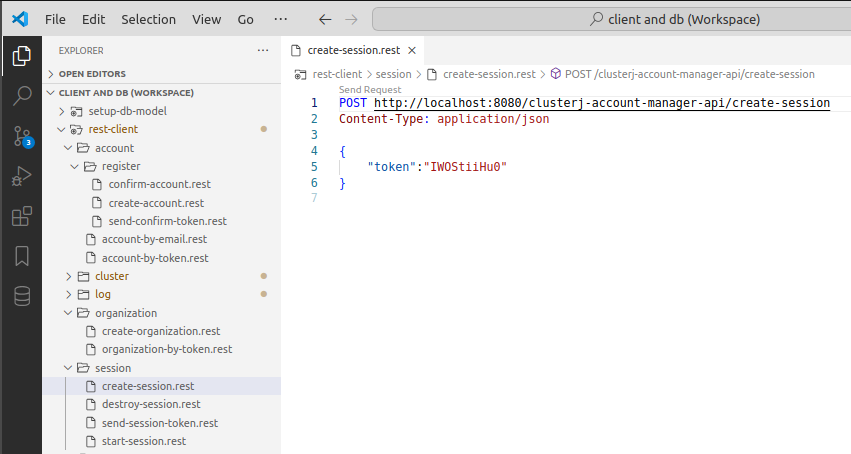
ClusterJ Session
To perform operations on ClusterJ setup, you got to have a session created with the clusterj-account-manager.war endpoints:
- Create session endpoint
- Send session token endpoint
- Start session endpoint
After you’re finished with the session, logout from ClusterJ:
- Destroy session endpoint
- Delete the email with the token